Capital One Got Hacked: Is The Cloud Actually Secure?
Just a few weeks ago, the news broke that Capital One Financial Corporation had suffered a massive data breach that affected 100 million individuals in the United States and approximately 6 million in Canada (https://www.capitalone.com/facts2019/). The hacker alleged to be responsible is Paige Thompson (aka “erratic”) from Seattle, Washington.
Although the criminal complaint (https://www.justice.gov/usao-wdwa/united-states-v-paige-thompson) conspicuously omits the name of the “Cloud Computing Company” where Capital One’s data was compromised, it’s well known in the tech world that Capital One is a large customer of Amazon Web Services - they’re even featured in multiple enterprise case studies on AWS’ website (https://aws.amazon.com/solutions/case-studies/enterprise/). Further evidence can be found in the complaint, which uses familiar AWS Simple Storage Service (S3) terminology when discussing “storage buckets” and the “list buckets command.” So, there’s little doubt (at least in my mind) that the data was comprised on AWS S3 through an IAM Role that had broader permissions than it probably should have. In short, Capital One left a backdoor open to a mountain of data.
With both a major financial institution and the world’s largest cloud provider implicated in a large-scale data breach, lots of people are rightfully asking the question: is the cloud secure?
Here’s my answer: Cloud platforms have proven themselves secure, especially major providers such as AWS, Azure, and Google Cloud. However, what their customers build on top of these cloud platforms are, at times, not. At the end of the day, cloud providers offer an overall security benefit to customers by enabling them to focus on developing and securing their applications instead of the entire infrastructure stack.
With regards to this specific incident, there was no inherent vulnerability in AWS that was exploited as part of the attack (at least none identified by the FBI cyber forensics team). Instead, the attack exploited Capital One’s poor configuration of AWS tools such as Web Application Firewalls (WAF), Identity Access Management Roles (IAM Roles), and S3 bucket policies.
Looking at the bigger picture, AWS and other major cloud providers have undergone rigorous cybersecurity audits and have received certification to host sensitive financial information, health records, and even classified government data. These audits look not just at encryption protocols and technology, but also human processes and access controls.
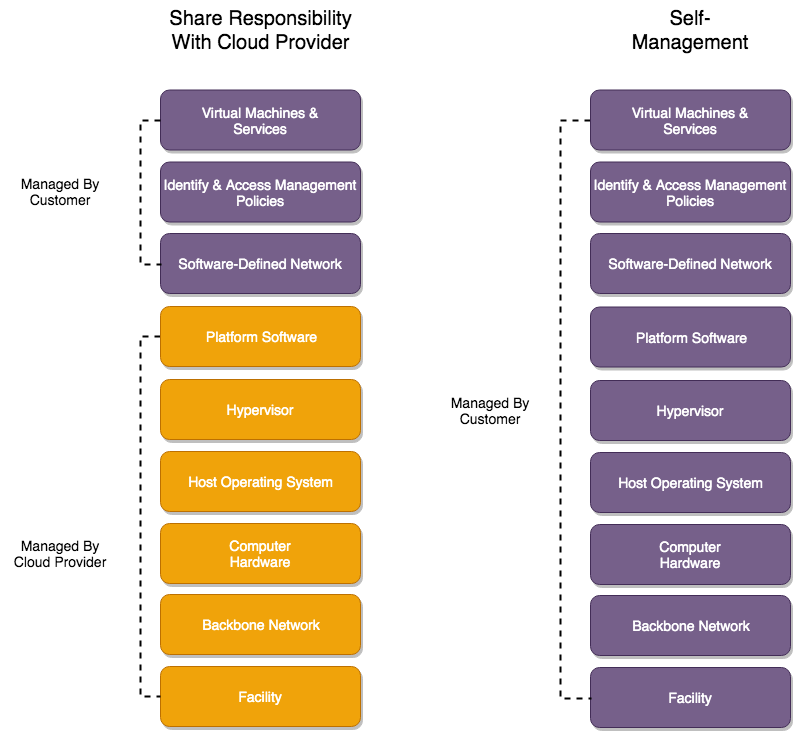
Each year, cloud providers spend $Millions, even $Billions, to develop secure infrastructure, platforms, and software, which saves customers from making such investments themselves. Instead, companies can rent these secure capabilities on demand and focus on the core competencies of their business, which is developing applications for their own customers. This is known as the Shared Responsibility Model: cloud providers focus on developing and securing the cloud platform, while customers are responsible for securing the services they build on top. This is actually a security benefit of operating in the cloud because customers are responsible for protecting only a small subset of the infrastructure required to run a modern application.
The diagram below depicts some of the concerns delegated to the cloud provider and customer under the Shared Responsibility Model, versus the alternative of self-managing an on-premise cloud.
In light of this comparison, if companies struggle to operate securely with the majority of concerns delegated to the cloud provider, they’re unlikely to do a better job if they have to secure the entire stack - from physical infrastructure all the way up to the application layer. According to Verizon’s 2019 Data Breach Investigations Report (https://enterprise.verizon.com/resources/reports/dbir/), web applications and command and control systems (administrative tools) comprise over 80% of the vectors involved in data breaches, and they’re most commonly compromised through (1) phishing, (2) stolen credentials, and (3) backdoors. Preventing these forms of data breach fall squarely within the customer’s zone of responsibility whether they use a public cloud provider or not.
Still, one question remains: If the cloud is so secure, then why are we hearing about these cloud customers getting hacked? The reason is that more workloads are moving to the cloud because of the benefits it offers. Nonetheless, the root cause of these incidents has, and will likely remain the same, and it’s not unique to the cloud. Of course, I’m talking about human nature. Companies and their employees are under constant pressure to deliver new features to their customers and remain competitive in the market. Therefore, security concerns are at times a secondary consideration to speed. Also, companies are constantly defending against attacks levied by hackers around the world, and it’s a challenge to keep up with new threats and remain vigilant. At the end of the day, hackers will continue to exploit the same old weak links, which are the people and software responsible for delivering end-user features, and not the underlying 3rd party platforms.